18 July 2023
Content Provided by DroneShield
What technique best defeats rogue drones? This question has surged into importance as threats from drones—becoming more and more capable and accessible—continue to increase dramatically.
Counter-drone technologies are evolving quickly to stay ahead of the threat, offering capabilities to detect, identify, track—and sometimes defeat—rogue drones using various technologies. Whether to include a defeat capability in a counter-drone installation—and if so, which type—poses a special challenge due to the diversity of defeat technologies and the complex regulatory and liability environment.
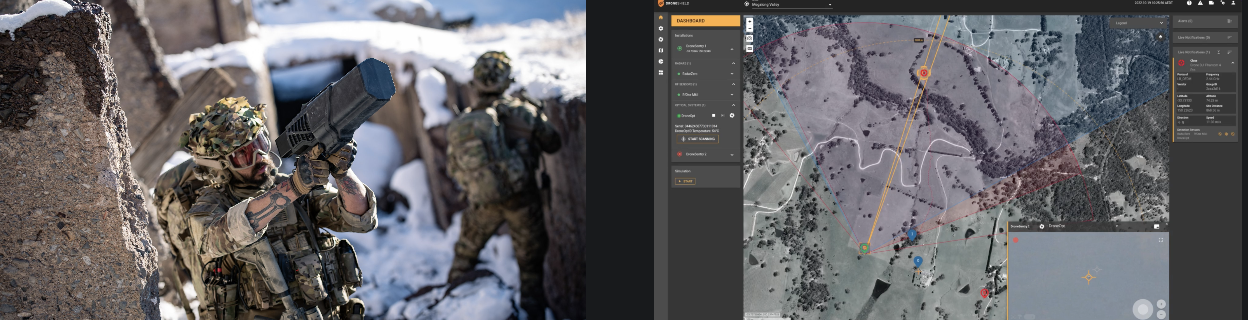
In many operational scenarios, drone defeat can be overkill, with optimal protection provided by a passive, undetectable solution that reliably detects, identifies and locates drones and their operators for immediate response by security personnel. Such solutions generally rely on passive Radio Frequency Direction Finding sensors, sometimes supplemented by day/night optical and thermal cameras.
When operationally required, drone defeat technologies fall into two broad categories. Hard-kill defeat, primarily in the domain of military applications, physically destroys or disables the drone but risks collateral injury or damage. Soft-kill defeat safely renders the drone harmless by disrupting its use of the Radio Frequency (RF) spectrum.
Most drones rely on RF to send and receive operator control signals, transmit their video feed and navigate via GPS and other satellite constellations. Two soft-kill RF-disruption techniques have emerged: RF cyber takeover and RF jamming. Each brings advantages and disadvantages, yet the two could be complementary for specific high-threat applications.
RF Cyber Takeover Defeat
RF cyber takeover relies on previous reverse-engineering of the stream of commands—if unencrypted—sent between the operator and a specific make or model of drone. When that drone is encountered again, the solution manipulates the RF protocol to override the drone operator’s commands with its own. When it works, the results are impressive: complete control over the drone that can, for example, force it to land in a safe location. This capability can make RF cyber takeover a worthwhile addition to a layered counter-drone defeat component.
However, because of its weaknesses, there are risks in relying on RF cyber takeover as the sole defeat component:
-
It’s strictly library-based, and a novel drone communicating using an unknown protocol will be immune.
-
Drones with encrypted controller communications will be immune.
-
The solution is susceptible to manufacturer protocol changes; the solution may become ineffective until manufacturer updates are once again reverse-engineered—unless the manufacturer adds encryption, in which case that drone will become immune.
-
Such solutions frequently control rogue drones only serially—one at a time—taking seconds or sometimes minutes per drone, making them less effective against swarming drone threats.
-
When a technique is ineffective against a particular class of drones, as with cyber takeover’s inability to defeat encrypted-communications drones, bad actors have demonstrated the real-world ability to quickly learn and adapt by switching drone models.
Legal considerations: if the cyber takeover system also relies on communications interception and decoding for a detection component, it falls afoul of specific wiretapping laws like those in the United States. It would therefore be unlawful to use, even for detection only, except by authorized agencies during special national security events.
RF Signal Jamming Defeat
The other soft-kill RF disruption technique, RF signal jamming, can sever three different RF links needed for a drone to remain effective: the operator-to-drone command stream, the drone-to-operator First-Person Video (FPV) stream, and/or the Global Navigational Satellite System (GNSS) reception the drone relies upon for wayfinding.
Depending on the make and model of the drone, jamming the GNSS reception or command stream will result in the drone slowly landing, returning to home, or hovering until battery depletion and then slowly landing. In any event, once jamming is activated, the drone threat is neutralized. Because RF signal jamming doesn’t depend on signature libraries or previous reverse engineering, it reliably defeats a much broader array of drone makes and models while remaining unaffected by manufacturer updates to their protocols or signal encryption. It is much more likely to instantly neutralize a more comprehensive array of drones than RF cyber takeover, plus it simultaneously neutralizes all drones in a swarm.
Selected and deployed correctly, RF signal jamming technologies minimize unwanted collateral effects, for example, in airport environments. Jamming the operator-to-drone control signal defeats most drones, making airport-unfriendly GNSS jamming unnecessary. Today’s RF signal jamming can target its effects to 90-degree quadrants, while imminent advancements will make it surgical, limiting the effects to specific targets. Finally, quick defeat means RF signal jamming needs to be activated only briefly.
Choosing a Solution
Organizations considering adding soft-kill drone defeat to their counter-drone system can inform their decision by carefully weighing their threat profile against each drone-defeat technique’s costs, strengths and weaknesses. For example, many organizations may be better served by investing in a robust, passive drone-detection system rather than drone defeat.
When RF-based drone defeat is needed—and legally permissible—then the pros and cons of the two RF defeat techniques bear consideration. For example, is it acceptable to sacrifice the ability to defeat certain drones, as cyber takeover does, with the benefit of being able to redirect the remaining supported subset of drones? Or is it better to more-reliably neutralize a wider array of drones, as signal jamming does, and minimize the opportunities for bad actors to adapt and evade by switching drone models?
Organizations with the highest threat profiles may invest in both defeat technologies as part of a layered defense. If a rogue drone can’t be controlled by cyber takeover, then it could be defeated by signal jamming.
The final consideration is to choose a counter-drone Command-and-Control (C2) platform that is vendor-agnostic, capable of integrating with drone detection sensors and defeat effectors regardless of vendor. This future-proofs the initial investment while granting the flexibility to incorporate new best-of-breed technologies as they emerge.